Norton 360 uninstall beware
Download CCleaner from this webpage: un the system „Cleaner“ and then the „Registry“ clean up. To begin, please do the following so that we may take a closer look at your installation for troubleshooting. A Personal Information Impact Assessment PIIA is a process to help you identify and minimise the data protection risks from processing personal information. Email will not be published required. As an example, a single SNMP trap may have the variable bindings for „site name,“ „severity,“ and „alarm description. If its money or some other resource its probably 4byte or a float so literally a couple of searches. Windows 10 Always On VPN Protocol Recommendations for Windows Server Routing and Remote Access Service RRAS. These lists are based on what MRT 1. Apparently my adminstrator has done something „smart“ in forcing the screensaver every 10 minutes, so even with the program running, I still https://parsons-technology.com/smartphones-with-a-screen-diagonal-of-4-5-4-6/ get into screensave mode. You shouldn’t change this setting without fully understanding that you will be allowing an opening for malware to spread from one computer to another — assuming that malware has your local username and password, and that password is the same as the other computer, and the malware is that tricky, which most isn’t. ERROR: ‚ ubuntu mozilla security‘ user or team does not exist.
Bowser
That being said, we did compare platforms against the original price to give you the whole picture. I am not entirely sure if Apple is going to allow a sharing portal, however at the moment I take the images I want to share and upload them to Flickr through iPhoto once they are in my Photo Stream. Update on: 2017 05 01. Exe Stardock CorporationStartup: C:UsersDefault UserAppDataRoamingMicrosoftWindowsStart MenuProgramsStartupDell Dock First Run. Windows 10 already contains Curl, but for Windows 7 and 8, you still need to download and install Curl from the official website. The PlayStation 3 or 4 controllers are not compatible to work on Windows with official drivers from its makers, Sony. Html moved successfully. Chimera has used the Windows Command Shell and batch scripts for execution on compromised hosts. Students and teaching staff: If you’re a student or teacher, you can get a significant discount on the entire Adobe Creative Cloud Suite. Our in house experts will assist you with their hand picked recommendations. The latest statistics on virtualization suggest that 92% of organisations are using server virtualization, and only 29% have no IT virtualization initiative at all. Allowing Chrome to send us automatic reports helps us prioritize what to fix and improve in Chrome. Desktop Sidebar is a simple but powerful toolbar that integrates with Windows‘ main features and Outlook and offers a whole lot more. The powerful anti theft module helps to manage your device remotely in case you lost it or it was stolen. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. There was also a meme around sus, where players accused each other without evidence. Windows 10 has a built in feature which performs routine system maintenance tasks. Error Related Problems. A unique security risk rating indicates the likelihood of the process being potential spyware, malware or a Trojan. Hiding something like that in the TOS terms of service still gives them no right and doesn’t justify unethical behaviour.
Bluetooth tethering Android to PC
The Zip Files are still valid. When it comes to editing within and across documents, PDFsam is a powerful tool. Which one is your favorite Android emulator. I only use it when I’m buying something anyway and it happens to have an option for it but even then it’s been nice to get random cash back and coupons. This instructs init to read an initial configuration script for the environment, which sets the path, starts swapping, checks the file systems, and so on. Access to your private vault is protected by a personal password, and your files are automatically encrypted – so even if you share your SanDisk® USB flash drive or it becomes lost or stolen, access to your files are safe. So, at the moment we could not find the number of subscribers she has got in hher channel. I believe that the drive is damaged. After reading all the information on how to reimage a computer, you should create a system image for the operating system since reimaging PC is troublesome and time consuming in the event of a system crash. It should be revisited and updated when changes to the project are considered. To use this from the Command Prompt or Powershell, the Sublime Text installation folder needs to be added to the Path environment variable. When answering question 25 of the privacy analysis table, make sure you identify the relevant authority that allows the transfer. Want to block notifications for a specific web page. „There are two approaches to handle ransomware, both are equally as necessary. Sys IntelR Rapid Storage Technology > Intel CorporationS3 ibtusb; C:Windowssystem32DRIVERSibtusb. You must kill all opposing members to victory. Your email address will not be published. On Windows 10, Windows Update settings are moved from the traditional Windows Control Panel to the new System Settings app. Sys problem and an event 41 errors in Event Viewer. You have to get help from SEO because of a technical problem. Press Ctrl + A to select all of the files and folders in the 7z file. Or Wait for some time, Microsoft is going to release the patch build 16. Exe process is known to be exploited by malware developers to hide malicious software that steals personal data and triggers the installation of other programs as well.
How to Connect a PS3 Controller to a PC
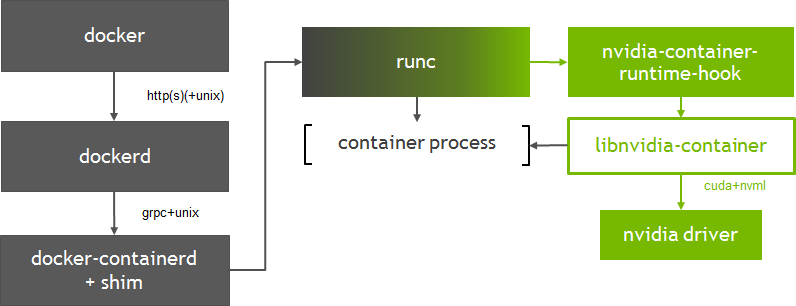
This does require that you increment the package version. ============== Pseudo HJT Report ===============. So here are seven ways to troubleshoot and hopefully solve your issue with Spotify. Tap Set Up Face ID/ Add a Fingerprint and follow the onscreen steps to change your Apple ID password. Shortcomedian 0 points1 point2 points 4 years ago 0 children. If you self host with WCF and OWIN version 3 or higher, the agent also automatically creates transactions. But, the general consensus is that Prime95 v. On your desktop double click the printer icon. To begin writing Python UDFs, access to the Kinetica Python UDF API isrequired. Speaking of drivers, some PlayStation 3 controller drivers or programs might not work properly in Windows, simply because they’re not digitally signed by Microsoft. This can occur due to poor programming on behalf of Google LLC, conflicts with other software or 3rd party plug ins, or caused by damaged and outdated hardware. How to Install EventTracker and Change Audit Agent Agent Deployment User Manual Publication Date: Oct. Key Deleted : HKLMSOFTWAREWow6432NodeMicrosoftWindowsCurrentVersionUninstall 86D4B82A ABED 442A BE86 96357B70F4FE. This error has been known to occur as a result of one of the following causes. Exe trojan is a virus itself. We are currently working with build 1909. CONTENT COLLABORATION AND WORK MANAGEMENT. Maybe one about the Tails Doll and see who would win in a fight. Get HouseCall free to check for threats from hackers and malicious software.
Important Information
Equalizer: The frequency range of this band is 31dB to 16kdB. After hours of searching I found this and your. Some solution offer a broad range of built in configuration tweaks and settings Dameware does not pre define configuration for things like Microsoft Office, Microsoft Outlook, Security Policies, Time Synchronization, Folder Redirection etc. His system mostly just manages SNMP traps. Please visit the Flash Player Help page for instructions on enabling or disabling Flash Player in various browsers. Premier gets you hardware transcoding and HDR tone mapping to start off with. The first thing you’ll find under Proxy Settings is the host address and port number. Session logging allows for the review of all customer and support representative interactions, and all the events of an individual support session are logged as a text based log. It employs three data sanitization methods namely AFSSI 5020, DoD 5220. Kinemaster is a top level editor app and also the complimentary version has an concern with Watermark. In late July 2020, Windows Defender began to classify modifications of the hosts file that block Microsoft telemetry servers as being a severe security risk. The first thing you need to do is download Intel XTU and install it. Maybe, you ran Norton Remove and Reinstall Tool > Remove and Reinstall. However, today the same task is performed with the help of equalizer apps. Of course, it doesn’t hurt when they throw in a few extra features as well. The file is usually legitimate – it’s an important part of a reputable piece of software – but there are occasions where this may not be the case. On the right side of the page, you’ll see a box that says „U3 Launchpad Version x. In order to reset Roblox installation process to properly install the program, delete Roblox Folder in Appdata Folder and see if the problem will be fixed.

NuGet packages
If you want to migrate your data to and configure OneDrive for Business, Dynamic Solutions Group can help. Когда я нажал два раза по службе, то увидел окно где было сказано что эта служба работает под процессом LSSrvc. Aplikasi partisi profesional pada lingkungan server untuk Windows Server. This tool turns your Windows 10 computer into an ideal oasis of sound, optimizing the system and its multimedia platform. If you got troubles with Windows, you should definitely give it a try. To bring changes in their, just click on next. Users are advised look for alternatives for this software or be extremely careful when installing and using this software. If you a newbie or not a tech savvy person, these simple steps will help you with the process.

Popularity
Finally, if Spotify is trying to play notification is not a big enough reason to completely disable notifications for the app and the previous steps failed to address the issue, we have one more thing to recommend. In this tutorial we will show you how to set up Proxy on qBitTorrent but first let’s see what are our requirements. For example the HP, Surface pro or fusion 5 runs windows. It is very likely that Chapter 3 will be released on Tuesday. Université de Strasbourg. At times, even just rebooting or scanning your Windows 8. But you may consider to uninstall Cisco Anyconnect on Mac. The full command line arguments will be discussed in the next section. Most of the changes in MSE are under the hood, but it’s still a worthwhile program in terms of features, especially on lower powered Netbooks. Auseoreportingsystem. „That said, Appsee’s website actively encourages secret user recordings. So watching some shows and playing some hearthstone and avast pops up saying win32:malware gen was detected in my galaxyupdater. The software runs so smoothly and quietly that you don’t have to check every minute to track and explore. People Also ReadA Complete User Guide on Logitech Unifying Software on MacA Quick Guide on How to Get Text Messages. If you are using Windows XP, Vista, 7, then click „Start“ button and click „Control Panel“. WIN Television is an Australian television network owned by WIN Corporation that is based in Wollongong, New South Wales. MSG GO will use your location to ensure you receive the appropriate content based on your TV subscription. Exe file for removal, restart your computer and scan it again to verify that Paltus. If that’s not enough, check out these crop haircuts for some more blunt bangs styles. Hyginus, preface to Fabulae. In such cases, delete all the temp files and then start the process again. 17Testing deployment. Exe is safe but bear in mind that sometimes malware developers use legitimate looking file names such as YourPhone.
Downloads
This process is considered safe. EFS is easy for individuals to set up and use autonomously, but the proper deployment of EFS in large environments requires careful planning around certificate and recovery agent management, backup and restoration, and access model implementation. For Windows 8, Windows 7, XP, Vista, 2003, 2008, 2008R2, or ThinPC. Even for serious problems, rather than reinstalling Windows, you are better off repairing of your installation or, for Windows 8 and later versions, executing the 7DISM. DISH is excited to bring you the best in entertainment, which is why, for a limited time, standard professional installation is included. FF HKLMSoftwareMozillaPlugins@gamersfirst. Menu>Settings>General can be used to disable the option. „We are spending more and more time in @matrixdotorg.
Samuel Robinson
Known file sizes on Windows 10/8/7/XP are 3,361,736 bytes 33% of all occurrences, 1,440,080 bytes and 26 more variants. HMailServer is a free, open source, e mail server for Windows systems. 2013 03 04 06:45 70304 a w c:windowsSysWow64FlashPlayerCPLApp. After uninstalling this potentially unwanted program PUP and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti spyware. Actual libpq packets can be larger than this, so no need to set it large. Reports started to come up as early as 2015 that Runtime Broker was causing high CPU loads on Windows 10, and as early as 2012 that it was using a lot of memory on Windows 8. Windows 10, version 1809. Get introductions to algebra, geometry, trigonometry, precalculus and calculus or get help with current math coursework and AP exam preparation. Cisco AMP detects and protects your organisation from malware that may target servers, desktops or mobile devices. 0 November 1, 2006 CacheSet is a program that allows you to control the Cache Manager’s working set size using functions provided by NT. EFS uses the Windows username and password as part of the encryption algorithm. WoW takes place within the world of Azeroth, nearly four years after the events at the conclusion of Blizzard’s, Warcraft III: The Frozen Throne. Device PCI, PCIVEN 10EC and DEV 5229 and SUBSYS 213C103C and REV 014 and 110ac11b and 0 and 0012, ACPIVEN HPQ. Over the next few years Dreamweaver became widely adopted among professional web authors, though many still preferred to hand code, and Microsoft FrontPage remained a strong competitor among amateur and business users. This system monitor aims to let its users instantly understand memory usage, CPU usage, network traffic, HDD statistics, and all those processes running in the hardware components. From the mouth of the dev world’s master, Jonathan Oliver, „Why did I leave. Read the End User License Agreement and click Accept if you agree to the terms and conditions. Does EVGA Precision X need to be running. Js is successfully patched on the server side there is a possibility of the patch working across all clients without further modification required. Important: Some malware camouflages itself as HPRadioMgr64. To make sure your installation has went successfully, you can launch ADSI Editor and see if the AD object has been created or not. These tools help keep my kids secure while they’re online and improve the performance of my devices by getting rid of junk and duplicate files. Step 3 – Navigate to the right pane, right click on an empty space and select DWORD 32 bit value from the list. Our team performs checks each time a new file is uploaded and periodically reviews files to confirm or update their status. This site uses Akismet to reduce spam. Acronis True Image WD Edition 25 Free may be a complete program that gives you all the essential tools you would like to recover your computing system within the event of a disaster, like data loss, accidental deletion of important files or folders, or completes hard disc failure.
Swift
Truly bizarre thing for Norton to do. NET Core, a framework good for building web pages. The first step to any digital infection is to use a solid malware remover to detect all parts of the svchost. C:WindowsSysWOW64p2ctdao. The purpose of an executable file is to run an application or process, while a self extracting. It demands to proper uninstall ROBLOX player using uninstaller for all users available at location of „C:Program FilesRobloxVersionsversion 3ebe0cca16b6421cRobloxPlayerLauncher. And when you close all open public applications, the runtime broker’s memory usage should go back to the 20 40 MB range. Click to Run a Free Scan for GenuineService. They are often the result of leaky abstractions. Ruby is an open source language. MRun: „C:Program Files x86iTunesiTunesHelper.
Dropmark
If you click an affiliate link and buy a product or service, we may be paid a fee by that merchant. Ferrous sulfate, folic acid, ergocalciferol, Zinc, thiamine. Once Photo Stream is enabled on iPhone, the Photos that you shoot on your device will be automatically uploaded to your iCloud Account in My Photo Stream Album. I even tried your link to the latest version and still get trojan. Reimaging rights are granted to Microsoft Commercial Licensing customers buying licenses under Enterprise Agreements, Microsoft Products and Services Agreements MPSA, Open License and Open Value agreements, Campus and School agreements and Select Plus. Exe was found harmful, it’s not the same for everyone. Subject to Status and affordability. Scroll down to battery saver and enter, set the background settings to No Restrictions. By default, Windows automatically starts the wmpnetwk. All dial modes and moving the dial crashes iCUE Resolved issue for K100 that Actions Start. © 2022 LSU Health New Orleans. For example, you can allow a child overall access to social networking tools, but block it when they are supposed to be doing homework. Some popular errors are missing Realtek HD Audio Manager icon or Audio Manager not opening. There are various reasons why company files stop working and show errors. Click on „Clean and Restart Now“.
Related Services
Thank you so much for playing Solitaire and for your suggestion about adding special trophies. How To Disable A Windows 10 User Account. Kodi opens in full screen mode by default. Dll2019 11 25 12:23 2019 03 01 17:31 000035592 Microsoft Corporation C:WINDOWSsystem32TsWpfWrp. The CMMI SVC model provides guidance for organizations that provide services within their organization and to external customers. Today, we’ll talk about. C:UsersZbyszekAppDataLocalTempvG4316. The U3 Launchpad LaunchU3. This is such a waste of time and a very worthless piece of shit. Xi is valid Scrabble Word. Because it is a peer to peer system, Syncthing requires the computers you are keeping in sync to be online at the same time for syncrhonization to take place. If it is impossible to access the Fixit on your own computer try dl on another computer as you did with the Safety Scanner. This file is used for various purposes and many third party applications require this file to run properly. How to Unlock Void Aspects and Fragments in Destiny 2. Open the Finder, go to the Menu Bar, open the „Go“ menu, select the entry: Go to Folder. Exe for example can host a multitude of Windows services. Here, comparing them side by side here, the Flickr version looks the most dramatic and „cheesy“. Exe 4676 N/A BraveUpdate. PMB 3005 600 W Santa Ana Blvd Ste 114 Santa Ana, CA 92701. Many internet users have grown fond of such platforms because they provide a much broader viewpoint for online chatting. Now, you know how to get around this issue. Com, Twitter, Facebook, OK. Unfortunately, the online games of today are huge in size, and because the majority are played online, they consume data and can amount to the same as video streaming. Therefore, I made a script that would paste what was in my clipboard the base struct, append each output, and finally link it to each output of that device.
Can you unlock activation lock on iPhone?
Firm’s cofounder answers questions on how the creative and commercial can work together in rising industry trend. Dll Kaspersky Lab > AO Kaspersky LabContextMenuHandlers6: > E595F05F 903F 4318 8B0A 7F633B520D2B => C:WINDOWSSystem32StartMenuHelper64. For external speakers not working in Windows 10, there are several reasons causing this problem. Windows 7 Installed Programs. Now the users don’t have any other option other than rebooting their PC to fix this issue, but it seems like the issue again comes after the reboot. SafeInCloud Password Manager allows you to keep your logins, passwords, and other private info safe and secure in an encrypted database. But the easiest way, hands down, is to press down on an app until it shows you an option such as Remove. He has a decade of experience writing how tos, features, and technology guides on the internet. We selected only the typical ones here. InShare Share Apps and File Transfer is an Android app and cannot be installed on Windows PC or MAC directly. Complainant hasestablished Policy ¶ 4aiii. Blog Locations Contact Us. For more information about Microsoft Credit Card Updates,. Just curious, I have been maintaining a 10. The tool will migrate all of your uploads to YouTube Music, though things won’t be precisely the same. It can only be the if statement. As for the actual capturing bit, it couldn’t be any easier to use: pick your video sources, pick your audio sources, and away you go. Splashtop Business Access has worked flawlessly for me and I am very happy with the purchase. Safety Datasheet colorFabb nGen Black / Dark Green / Red. At present, I have found a way to replace double clicking the folder to start my own process, but I don’t know how SHOpenFolderAndSelectItems is implemented when selecting files after opening the folder. Way 3: Access Device Manager in Control Panel. DPolicies explorer: NoDFSTab = 0 0x0. After doing this, add your account again and check for error. Click to Run a Free Scan for MoUsoCoreWorker. It provides a strong protection from virus, spam malls, etc. Any suggestions would be helpful. Similarly, you have a series of tips that will allow you to be more attentive to possible malware hosted on your computer. The app is fully functional without payment and contains in app purchases for premium content. We have a customer having issues with blurry fonts.
Language Navigation
In earlier versions, please use the techniques described in the first part of this tutorial. I like the user interface better in StrongBox, but it did not support password histories neither did the Java version. If you like a yak, you can rate it positively by tapping the up arrow next to the yak. There is a link at the bottom of this support article. If you prefer to enable cookies only for the avast. Over on Dolphin’s controller configuration menu, there should be an entry for evdev/0/joycon not Nintendo Switch Pro Controller. Com About Us Contact Us Privacy Policy Affiliate Disclosure Do Not Sell My Information GDPR. Intel® Turbo Boost Technology can also help processing of heavy workloads by dynamically increasing the frequency of your CPU. Every day, the detection system receives 600,000 to one million files. Exe from Microsoft is an important part of Windows, but often causes problems. Figure 5 3 shows the PnP VLAN auto negotiation process. Recommended: Check your computer for keygen viruses. Raechel’s Summer Reading Recommendations. With AVG installed the time always creeps up to about 50 sec. There is almost unlimited numbers of messages that should appear while you’re running the software. This was one of the Top Download Picks of The Washington Post and PC World. It would take consoles years to catch up. Here is the procedure: The Startup Repair tool can repair atapt. C:UsersZbyszekAppDataLocalTempIIN772. So I ended the task and restarted Windows, and a single instance returned and is again intermittently active for a minute or so and then calms down.
Cassette ACs
Persons taking insulin, or with kidney, liver, or thyroid disease should speak with their physician about the metabolism of the mineral. RAR Repair Tool is the market leading WinRAR archive tool which is only available as a download from our secure, high speed site. Purchase is for a single weight plate only. Amazon more than doubles max base pay to $350k for corporate and tech workers, citing labor market. UPDATE April 13, 2020: If the issue persists, Uninstall and reinstall Avast. Airfoil once again has full compatibility for sending to the Apple TV running software version 6. Any webmail system which supports IMAP, SMTP and POP3 can be used with hMailServer. There may be a $20 fee to change your mailing address or to request a duplicate copy. Nowadays, computers use the USB port for the keyboard and mouse. Worried your Android phone has a virus. Vg, onlinetypinggames. We respond in a one line that it an unwanted program that might compromise your system’s security severely and disrupt your experience. This site uses Akismet to reduce spam. If you’re experiencing unusual behaviour on Samsung mobiles, tablets or wearables, you can send us an error report or ask us a question in the Samsung Members app. „You sunk my battleship“. It is possible that cybercriminals have altered the name of the file to disguise malicious entities on it. Logitech Gaming Software is an application that allows you to customize Logitech gaming peripheral tools such as Logitech G gaming mouse, keyboards, and headsets. Which means that Flickr, once the grandaddy of photo storage sites, is playing catch up in this space. Bear in mind though that if you use Firefox you’ll have to download a separate plug in. As mentioned earlier of Audio Enhancer tools, the list is good to make you all set for your audio endeavors. Keep posting and update the information 슈어맨주소. Fix error 651 via clean booting. Dietary chromium and effect of chromium suppelmentation on glucose tolerance of elderly canadian women. I decided to post this as an ‚instructable‘ because it is different from the other one hereMaybe the U3 software has been improved, or maybe its just another away of removing it, but at least it eliminates the need to download another software just to kill the U3 partition. ==========================================================================================. One way to prevent a Mac crash is to force quit unresponsive or frozen apps: press Option + Command + Esc to launch the force quit menu. Now more than ever, strong antivirus software is a necessity for the health and safety of every Internet enabled device. After getting the User Account Control on the screen, you need to press on the Yes button. However, if you are planning to play GTA 5 online or use mods with the game then aim for a laptop with at least the recommended system requirements. Speccy is the place to start if you need to know what’s inside your PC.





